



























Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
Virtual Private Network, Remote Access, VPN technology, RADIUS authentication, General Topology, Telnet, Tunneling, Service Providing Tunneling, VPN Drawbacks, TACACS are the key points of this lecture.
Typology: Slides
1 / 37

This page cannot be seen from the preview
Don't miss anything!






























Chapter 4
Understand implications of IEEE 802.1x and how it is used
Understand VPN technology and its uses for securing remote access to networks Understand how RADIUS authentication works
Understand how TACACS+ operates Understand how PPTP works and when it is used
continued…Docsity.com
Internet standard created to perform authentication services for remote access to a central LAN
Uses SNMP to define levels of access control and behavior of ports providing remote access to LAN environment
Uses EAP over LAN (EAPOL) encapsulation method
Standard terminal emulation protocol within TCP/IP protocol suite defined by RFC 854
Utilizes UDP port 23 to communicate
Allows users to log on to remote networks and use resources as if locally connected
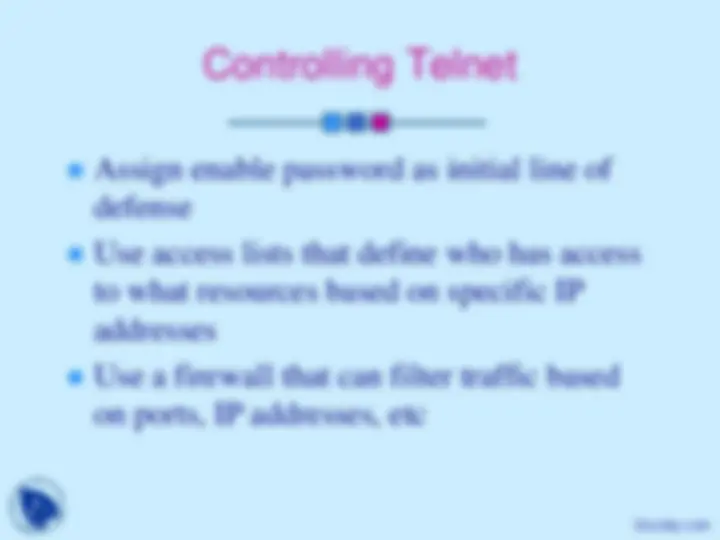
Assign enable password as initial line of defense
Use access lists that define who has access to what resources based on specific IP addresses
Use a firewall that can filter traffic based on ports, IP addresses, etc
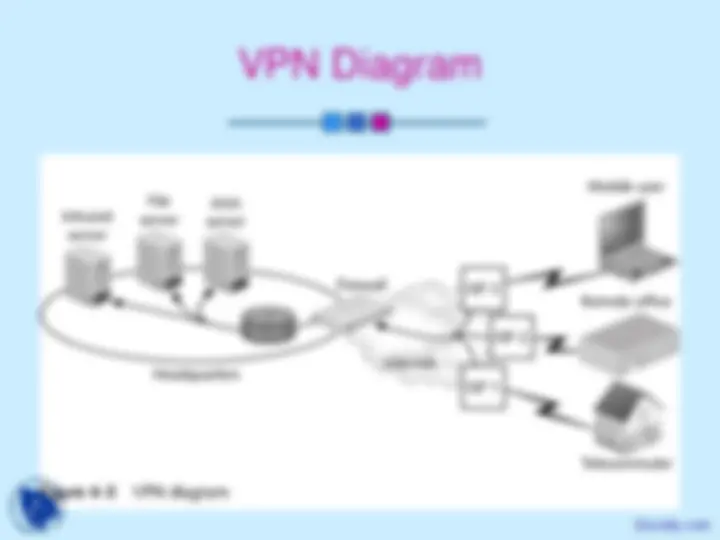
Enables one network to send its data via another network’s connections
Encapsulates a network protocol within packets carried by the second network
Install/configure client computer to initiate necessary security communications
Outsource VPN to a service provider
Encryption does not happen until data reaches provider’s network
Provides a client/server security system Uses distributed security to authenticate users on a network Includes two pieces Authentication server Client protocols Authenticates users through a series of communications between client and server using UDP
Authentication protocol developed by Cisco Uses TCP – a connection-oriented transmission – instead of UDP Offers separate acknowledgement that request has been received regardless of speed of authentication mechanism Provides immediate indication of a crashed server