














Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
Various methods for collecting business user requests and information for software development projects. Techniques include observational methods, interviews, and questionnaires. a step-by-step approach for using questionnaires and a list of potential questions for security considerations. It also includes a product management function description for an e-commerce website.
Typology: Papers
1 / 24

This page cannot be seen from the preview
Don't miss anything!

















PROGRAM TITLE: BTEC in Computing (Software Engineering)
UNIT TITLE: Software Development Lifecycles
ASSIGNMENT NUMBER: Assignment 2
ASSIGNMENT NAME: Software Development Lifecycles
SUBMISSION DATE: 7/7/
DATE RECEIVED: 7/7/
TUTORIAL LECTURER: Phạm Sơn Tùng
WORD COUNT:
STUDENT NAME:Nguyễn Lê Lợi STUDENT ID: BKC MOBILE NUMBER: 0363074734
Summative Feedback:
Internal verification:
Table of Contents LO3 Software development lifecycle implementation ............................................................ 5 P5 Perform software investigations to meet business needs. ............................................... 5 P6 Use appropriate software analysis tools/techniques to perform software investigations and generate supporting documentation. ......................................................................................... 10 LO4 Discuss the appropriateness of software behavior design techniques ........................... 20 P7 Discussion using examples of the appropriateness of software behavior design techniques ................................................................................................................................................... 20
LO3 Software development lifecycle implementation
P5 Perform software investigations to meet business needs.
Project analysis In order to obtain the data required for project development, interactions between designers and clients are required in every phase of scheme growth. The customer data on implementation issues should be searched and analyzed at every point. When analyzing feasibility, the broader questions are relatively general, for example: What is the scope of the problem, what is the best way to automate? No, or financial viability...
If we have to analyze the project-related information or project related objects during the analysis phase, then what feasible options can be used for the project and information. Details about this? There was a mistake. So how can we collect sufficient information to help develop applications?
Methods of collecting information Many common methods are employed to collect business users ' requests. There are a number of software system-specific techniques or some kind of user interface, some of which may be used in any working method.
Observational Method Developers often use observation techniques to leverage and evaluate data through professional observation and teaching, or working environments. This method is used to determine how requirements, growth possibilities or a business method can be identified, to establish and evaluate the effectiveness of a proposal, to recommend and to offer the highest quality alternatives for developing a design. Furthermore, this technique is often used together with other techniques to verify the precision of the information being collected.
There are two basic approaches to observation techniques: Active and passive Active Method: The investigator will ask any concerns concerning data about the problems necessary to create the software project when monitoring the method of operating on an object.
about the behavior of consumers. Nevertheless, the method of immediate contact has elevated price disadvantages; the interviewer has a lengthy history in leading and suggesting various questions during the debate.
Phone interviews and Mail interviews: Phone interviews: is an analysis subject method by telephone. The feasibility of this technique is increased with the support of technological equipment. High capability responses can be collected. The advantage of telephone interviews is that access to them is quick, easy to manage, regardless of distance. The downside of this technology is not suitable for complex interviews with nature; the behavior of changing objects is not observed.
Mail interview: is the technique by e-mail to the interviewee by issuing a questionnaire. The receiver simply has to check and send the questions to the interviewer. The benefit is that the designer does not need communication or negotiation skills because he is not faced with the test, the test findings are not partial. Costs for interviews are significantly smaller than for other interviews. The disadvantage of this method is that it is time consuming and not suitable for specialized problems.
Due to their own advantages and disadvantages in each data collection method. Consequently, individuals often merge various techniques for collecting and assessing the finest in project development.
Questionnaires/Surveys You must have excellent information if you want to get a nice research paper. And if you want excellent data, a nice questionnaire or study must be designed and implemented. Data collection techniques for generating a useful study paper are quite distinct.
The most prevalent and simplest study to do, however. This way you can create a survey, then submit it to many individuals, then use these responses for analyzing and evaluating infor mation.
In other words, you will use questions to rate your consent and usually ask questions like the image above in the questionnaire article. Moreover, you can also collect information by using YES / NO questions.
Good data collection. You have to make sure that those who reply to your questionnaire have to respond responsibly, seriously and not randomly. If too many people harass, the data you collect will not be different from a stack of waste and no good results. Then, how can good data collection be guaranteed?
An Up-to-date software will help a lot with security since almost all the visible bugs has been handled by a third-party company
SQL Injection
By using special character on the input, hacker can simply hack into the database system and cause damage to the data.
Error Messages
Too specific error message will give out a ton of information to the outsider – which in the beginning, does not need to know too much about the system
Validation of Data
Should be done from both side, server and client Passwords
The passwords must be long enough to keep the chance of being hacked low, the recommendation is at
least 8 characters with both number, normal, upper key and special character SSL
Passing personal information between client and server should be done through SSL protocol
P6 Use appropriate software analysis tools/techniques to perform software investigations and generate supporting documentation.
Stackholders:
Use case diagram
Entity relationship diagram:
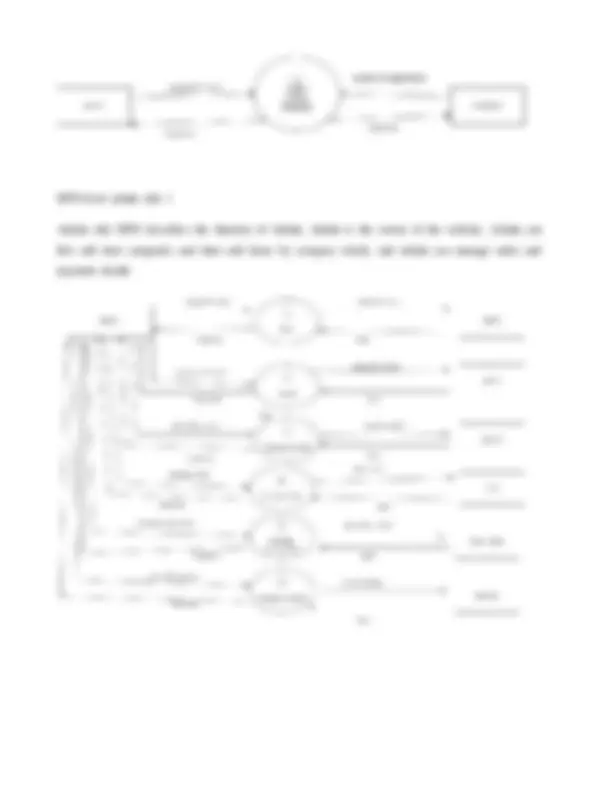
DFD context level - level 0
Context-level data flow diagrams (dfd) depict the entire system. Dfd level (o) describes all user modules that operate the system. Below is a data flow diagram of an online clothing purchase page showing that two users can operate the system as Administrator and Member User.
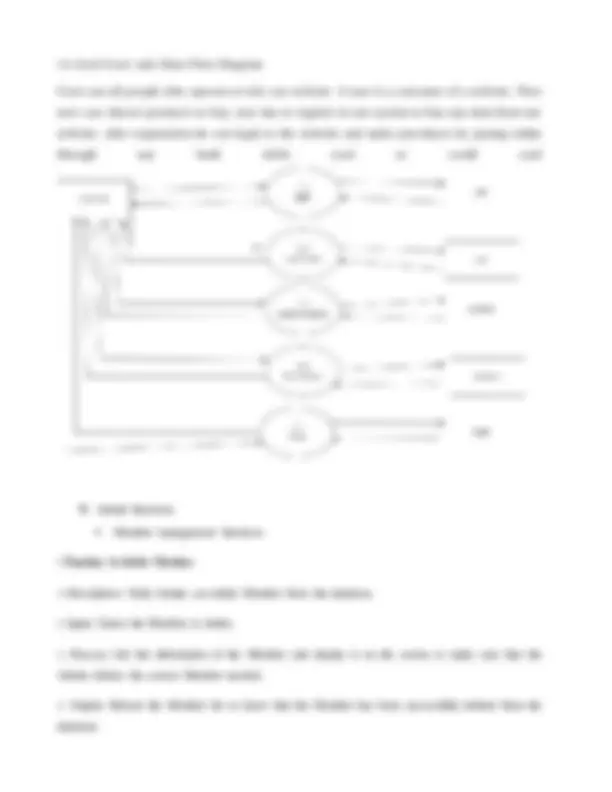
DFD level admin side 1
Admin side DFD describes the function of Admin, Admin is the owner of the website. Admin can first add item categories and then add items by category wisely. and admin can manage order and payment details
Product management functions
Description: Help Admin change the information of the product already in the database.
Input: Admin enters new product information.
Process: Update new information for the product.
Output: Display the product update notification.
Description: Help Admin can delete products
Input: Select the product to delete
Process: Delete in the database
Output: Reload the product list
Description: Help Admin can add new products.
Input: Admin enters the necessary information of the new product.
Process: Check which fields cannot be left blank. If all match then add to database. Otherwise, do not add to the database.
User administration functions
Description: Helps Admin can delete users.
Input: Find the User to delete and select the delete icon.
Process: Delete User from the database
Functions For Invoice Orders
Description: View order details in the database
Input: Select invoice name or customer name of that invoice.
Process: Get all the details of the order in the database.
Output: Display detailed information in the order.
Description: After the customer confirms the order, the invoice will be saved in the database. Admin calls customers to confirm information. If the invoice is correct, it will be transferred to the delivery department. After the successful transaction, the invoice is completed. In the process of processing the invoice, the customer can cancel the order.
Input: Admin selects the invoices to be processed
Process: Process changes of the invoice.
Output: Reload the invoice list to review the change of the invoice.
Client functions Membership registration function Description: For customers to register as a member to have more functions for buying and selling products, as well as creating a long-term relationship with the company. Thereby, members will enjoy special promotions.
Input: Visitors must enter all information (: is required information) User name: () Password: (*)
Input: After viewing the shopping cart, customers wishing to place an order online can click the order button and fill in some necessary information so that the administrator can confirm the information and deliver the goods directly to the customer. the correct address as quickly as possible.
Process: Save information about customers and order invoice information into tables in the database.
Output: Give notice that the order has been successfully or failed.
Login function
Description: For Member to login to the system.
Input: User enters information about username and password to login.
Process: Check the username and password entered by the user and compare with the username and password in the database.
Output: if true for login and display member functions, otherwise display a message asking to re-enter if the information is incorrect.
Logout function Description: Allows users to log out of the system when they no longer need to use the system.
Input: User clicks on the exit button on the system.
Process: Delete session to save login information to stop the session of Member account in the system.
Output: Return to the current page. Hide all member functions.
Password change function
The function of viewing invoices that have been created
LO4 Discuss the appropriateness of software behavior design techniques
P7 Discussion using examples of the appropriateness of software behavior design techniques
A request is simply a function, service, or feature that the user needs. They can also be constraints, procedures, business rules, or other functionality that a company needs to meet expected user requirements.
Functional requirements -Provide detailed information with visual product images Because this is an online shopping activity, customers cannot touch, touch or try the product, so providing complete and detailed information plays an important role in providing the user experience as well as shaping the product. The number of potential customers. Images also have a great impact on psychology and buying behavior, the more detailed the images, the more convenient it will be for customers to track, thereby increasing the possibility of ordering a lot. A note when taking photos is to take photos from different angles, as well as add a product zoom feature to give customers a more general and multi-dimensional view of the item.
-Filter search function One of the must-have features of an online sales website is the filter search function. Each customer visits your online sales website with different purchasing purposes. So, in order for customers to quickly get the information they want, your online sales website needs to have a search