

















Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
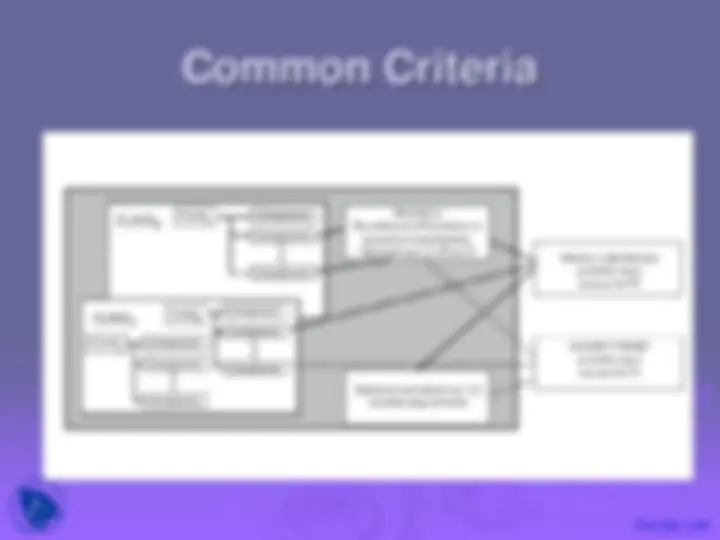
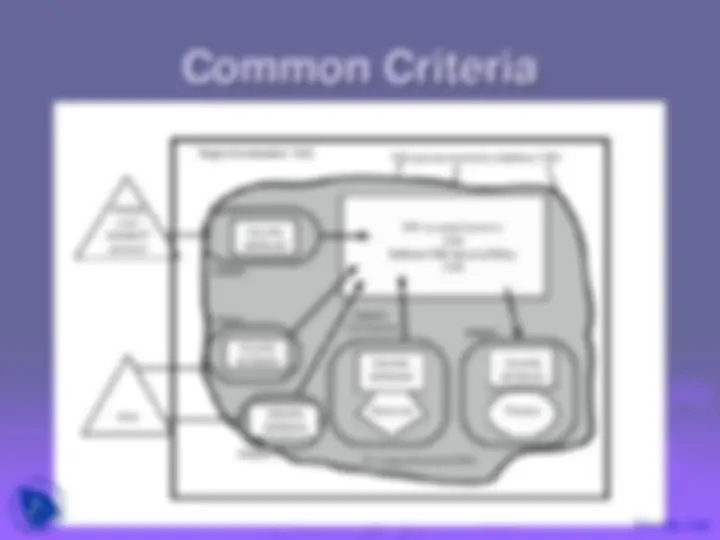
An in-depth understanding of firewalls, their role in network security, and their limitations. Topics covered include packet filters, stateful packet filters, application-level gateways, circuit-level gateways, and firewall configurations. Access control and trusted computer systems are also discussed. The document concludes with an overview of common criteria, an international initiative for specifying security requirements and evaluation criteria.
Typology: Slides
1 / 30

This page cannot be seen from the preview
Don't miss anything!























The function of a strong position is to make the forces holding it practically unassailable — On War, Carl Von Clausewitz
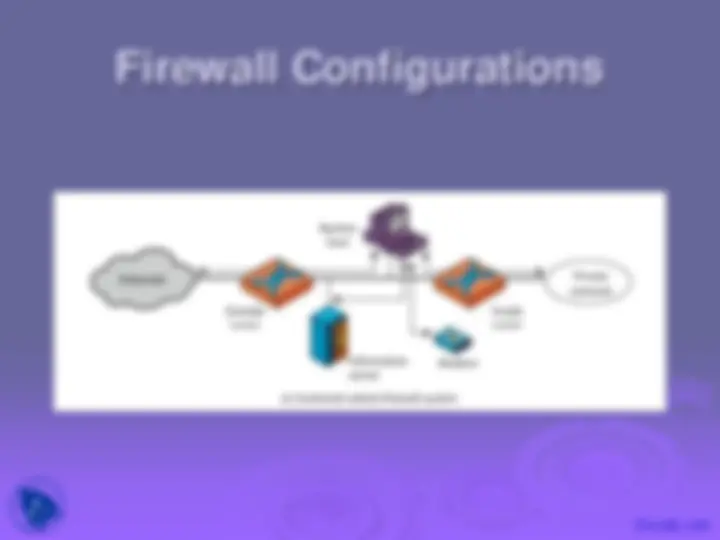
a choke point of control and monitoring
interconnects networks with differing trust
imposes restrictions on network services only authorized traffic is allowed
auditing and controlling access can implement alarms for abnormal behavior
provide NAT & usage monitoring
implement VPNs using IPSec
must be immune to penetration
cannot protect from attacks bypassing it
eg sneaker net, utility modems, trusted organisations, trusted services (eg SSL/SSH)
cannot protect against internal threats
eg disgruntled or colluding employees
cannot protect against transfer of all virus infected programs or files because of huge range of O/S & file types
traditional packet filters do not examine higher layer context ie matching return packets with outgoing flow
stateful packet filters address this need
they examine each IP packet in context keep track of client-server sessions check each packet validly belongs to one
hence are better able to detect bogus packets out of context
have application specific gateway / proxy
has full access to protocol
user requests service from proxy proxy validates request as legal then actions request and returns result to user can log / audit traffic at application level
need separate proxies for each service
some services naturally support proxying others are more problematic
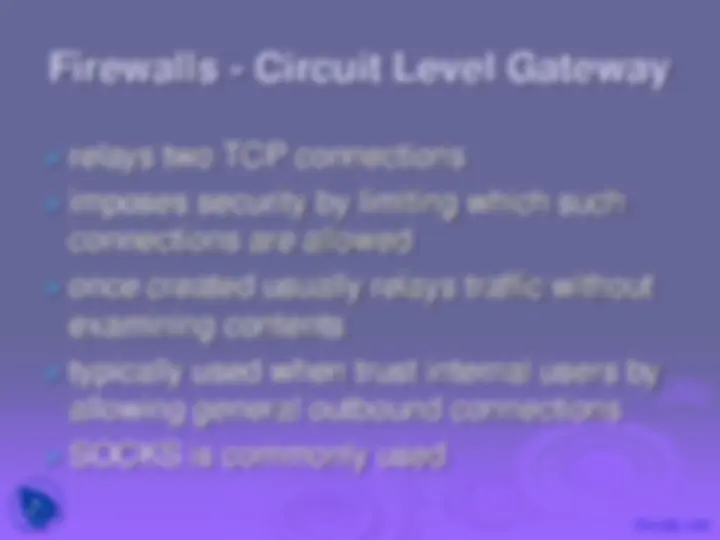
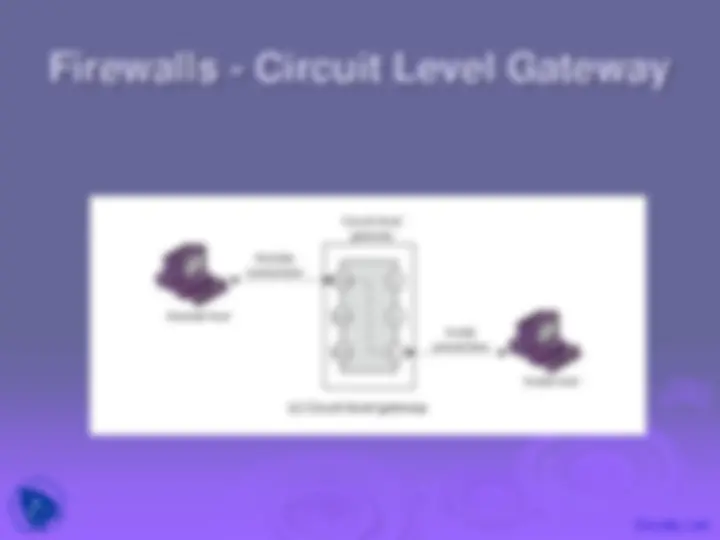
relays two TCP connections
imposes security by limiting which such connections are allowed
once created usually relays traffic without examining contents
typically used when trust internal users by allowing general outbound connections
SOCKS is commonly used
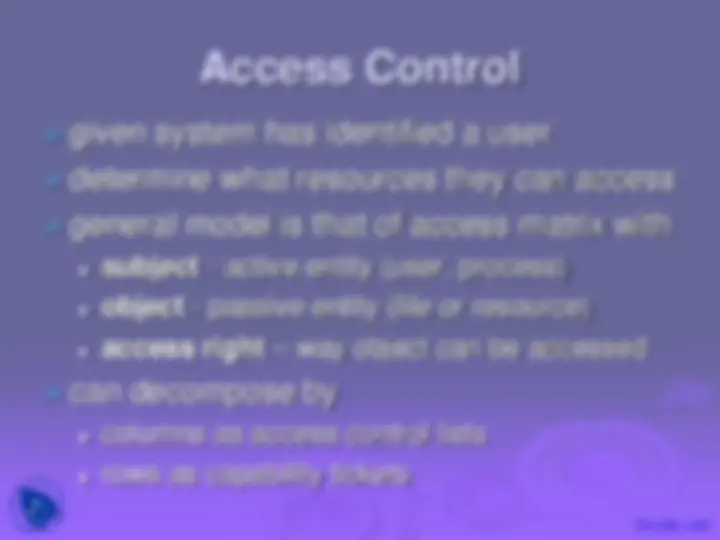
given system has identified a user
determine what resources they can access
general model is that of access matrix with
subject - active entity (user, process) object - passive entity (file or resource) access right – way object can be accessed
can decompose by
columns as access control lists rows as capability tickets