














Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
Finite Fields, Group, Cyclic Group, Ring, Field, Modular Arithmetic, Divisors, Arithmetic Operations, Greatest Common Divisor, Euclidean Algorithm, Galois Fields are the basic and key points you can learn in this lecture of Cryptography and Network Security.
Typology: Slides
1 / 31

This page cannot be seen from the preview
Don't miss anything!
























The next morning at daybreak, Star flew indoors, seemingly keen for a lesson. I said, "Tap eight." She did a brilliant exhibition, first tapping it in 4, 4, then giving me a hasty glance and doing it in 2, 2, 2, 2, before coming for her nut. It is astonishing that Star learned to count up to 8 with no difficulty, and of her own accord discovered that each number could be given with various different divisions, this leaving no doubt that she was consciously thinking each number. In fact, she did mental arithmetic, although unable, like humans, to name the numbers. But she learned to recognize their spoken names almost immediately and was able to remember the sounds of the names. Star is unique as a wild bird, who of her own free will pursued the science of numbers with keen interest and astonishing intelligence.
— Living with Birds , Len Howard
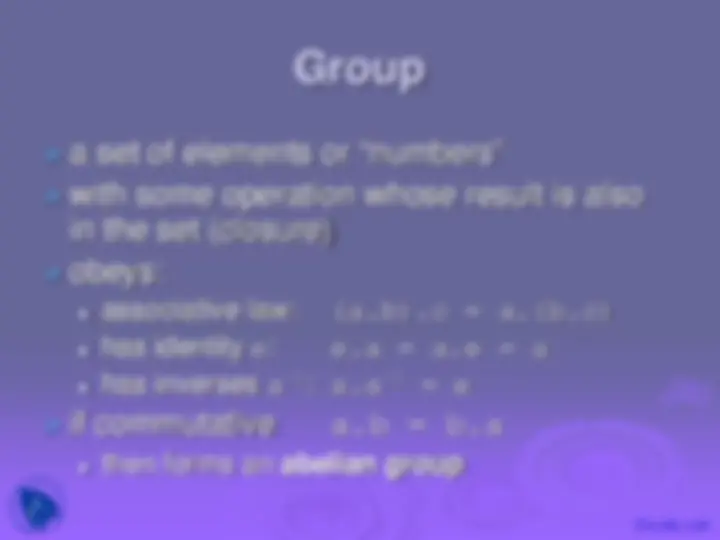
associative law: (a.b).c = a.(b.c) has identity e: e.a = a.e = a has inverses a-1: a.a-1^ = e
then forms an abelian group
example: a-3^ = a.a.a
ie b = ak^ for some a and every b in group
abelian group for addition abelian group for multiplication (ignoring 0)
ring
group -> ring -> field
define modulo operator “a mod n” to be
remainder when a is divided by n
use the term congruence for: a = b mod n
when divided by n, a & b have same remainder eg. 100 = 34 mod 11
b is called a residue of a mod n
since with integers can always write: a = qn + b usually chose smallest positive remainder as residue
a+b mod n = [a mod n + b mod n] mod n
can do modular arithmetic with any group of
integers: Zn = {0, 1, … , n-1}
form a commutative ring for addition
with a multiplicative identity
note some peculiarities
if (a+b)=(a+c) mod n then b=c mod n but if (a.b)=(a.c) mod n then b=c mod n only if a is relatively prime to n
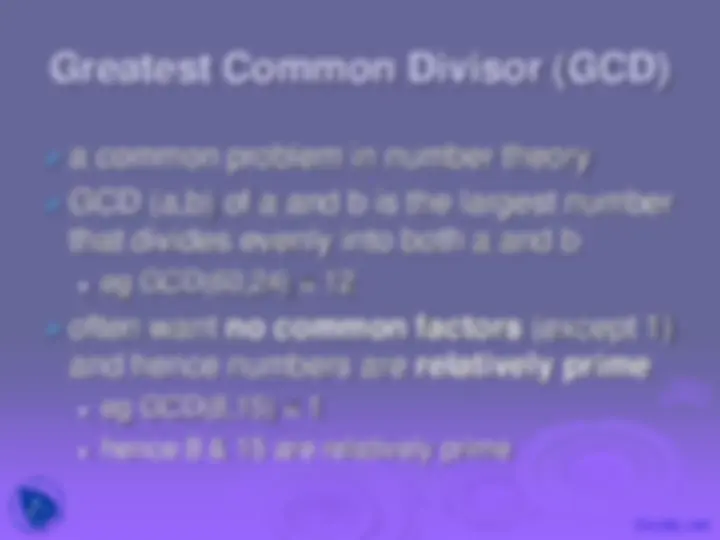
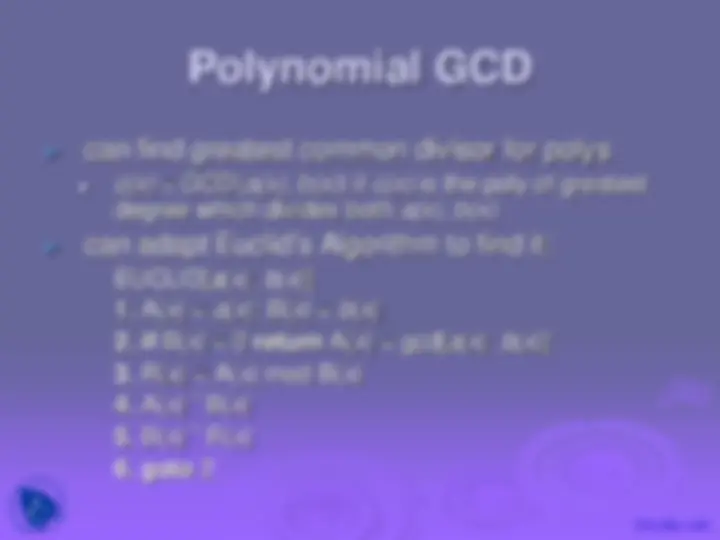
Greatest Common Divisor (GCD)
eg GCD(60,24) = 12
eg GCD(8,15) = 1
hence 8 & 15 are relatively prime
an efficient way to find the GCD(a,b)
uses theorem that:
GCD(a,b) = GCD(b, a mod b)
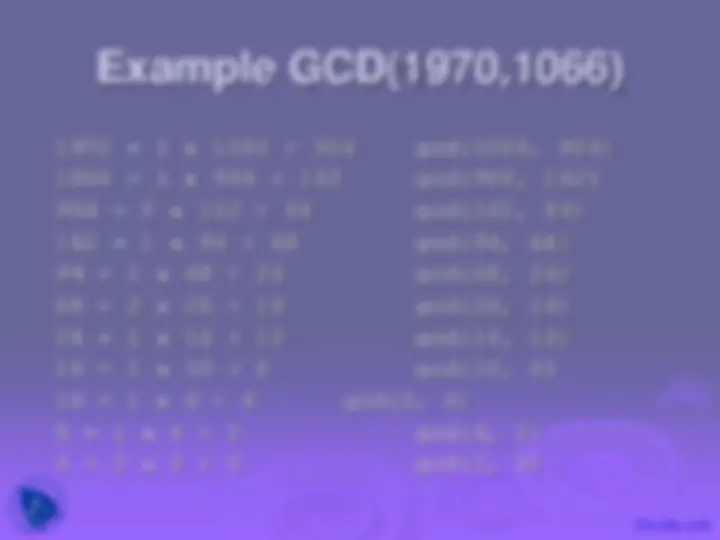
Euclidean Algorithm to compute GCD(a,b) is:
EUCLID(a,b)
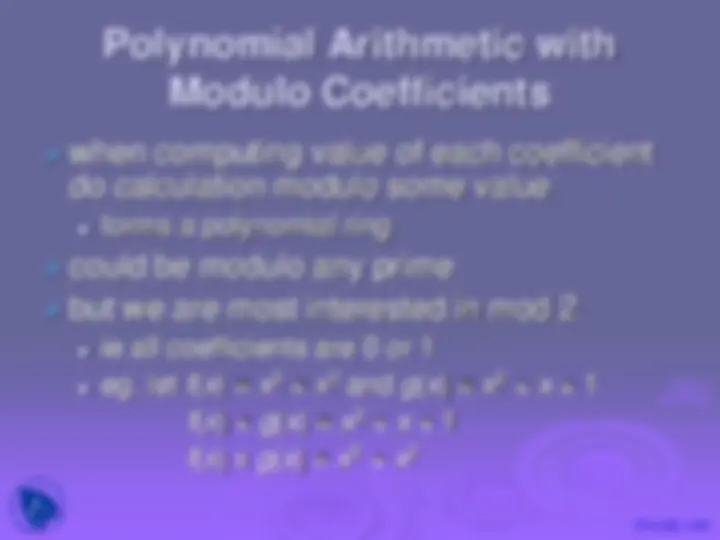
GF(p) GF(2 n^ )
since have multiplicative inverses
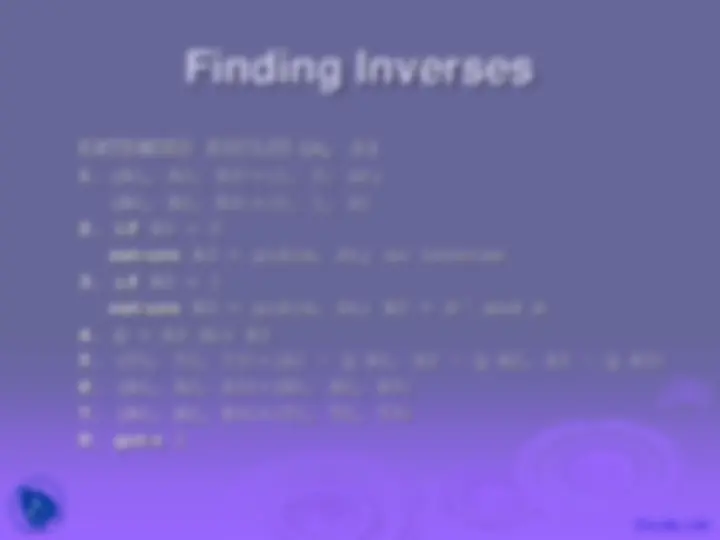
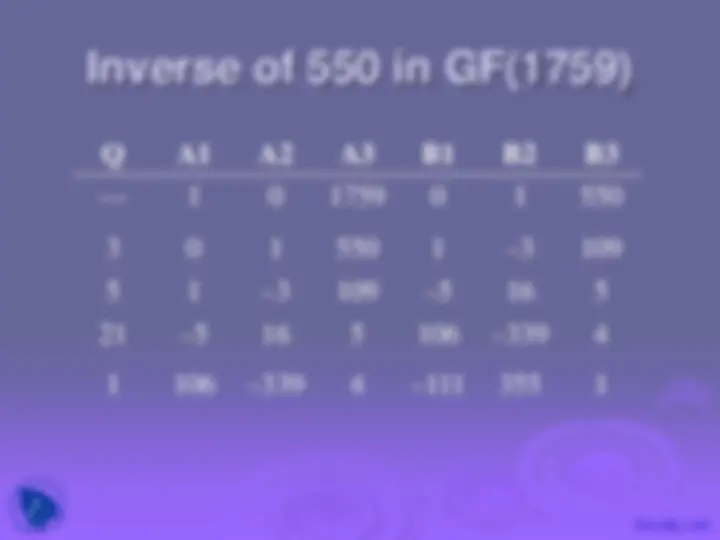
EXTENDED EUCLID( m , b )
1. (A1, A2, A3)=(1, 0, m ); (B1, B2, B3)=(0, 1, b ) 2. if B3 = 0 return A3 = gcd( m , b ); no inverse 3. if B3 = 1 return B3 = gcd( m , b ); B2 = b –1^ mod m 4. Q = A3 div B 5. (T1, T2, T3)=(A1 – Q B1, A2 – Q B2, A3 – Q B3) 6. (A1, A2, A3)=(B1, B2, B3) 7. (B1, B2, B3)=(T1, T2, T3) 8. goto 2