Download Distributed Information Systems Lecture 9 - Security and more Lecture notes Computers and Information technologies in PDF only on Docsity!
Security
Dr Simon Blake
Topics for this lecture
•^
Security^ – Significance / Importance of security– Threats and Attacks– Security techniques:
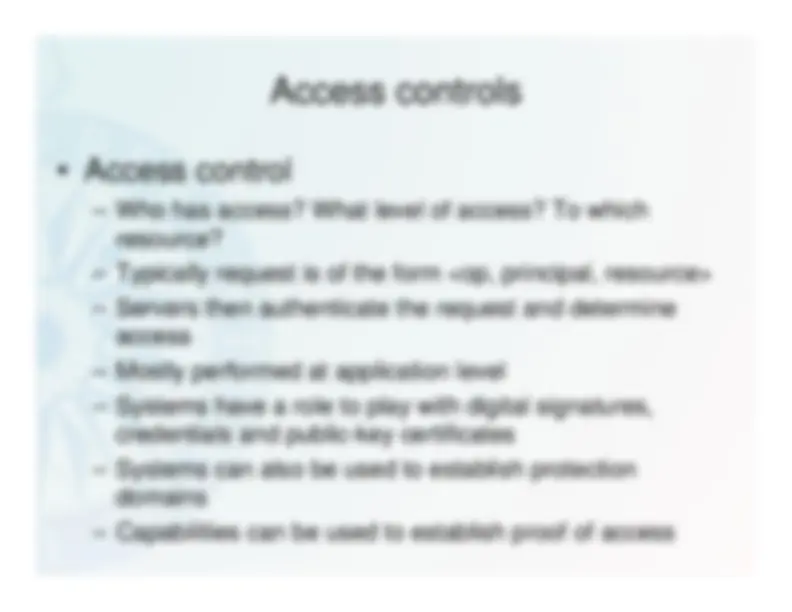
- Cryptography• Digital signatures• Certificates• Access control• Credentials
•^
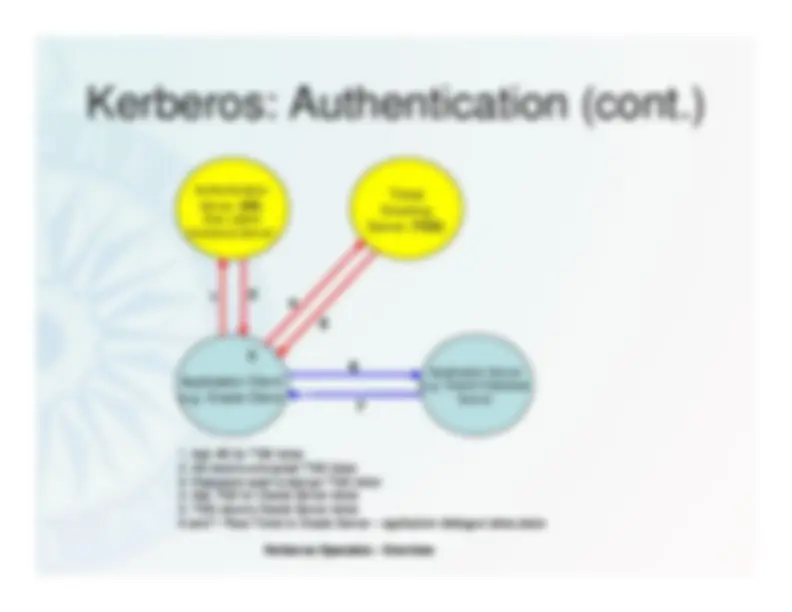
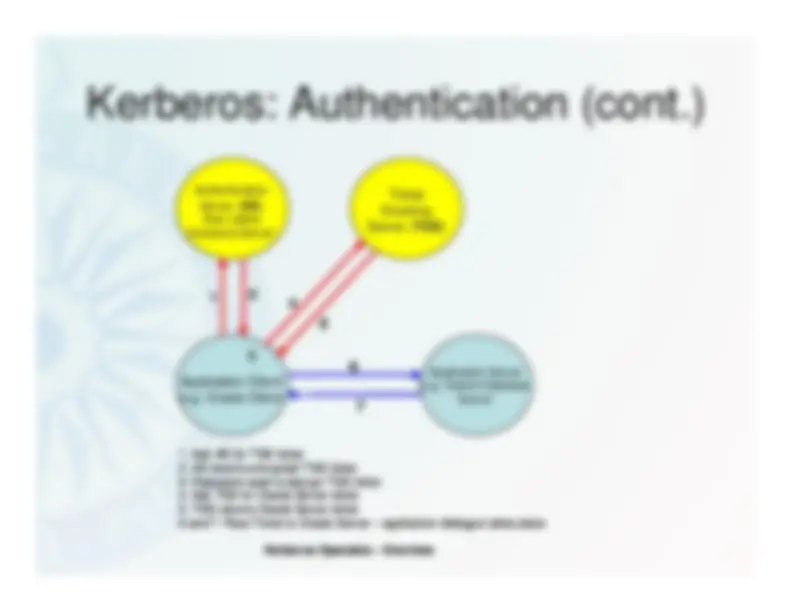
Kerberos^ – The architecture and operation of Kerberos
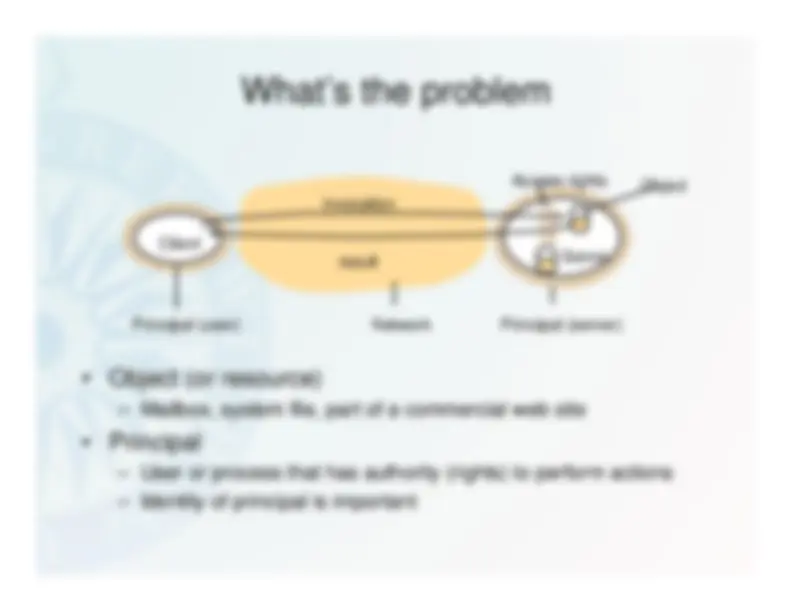
Security Requirements
• Secrecy (Confidentiality)• Data Integrity• Authentication• Non-repudiation• Availability• …
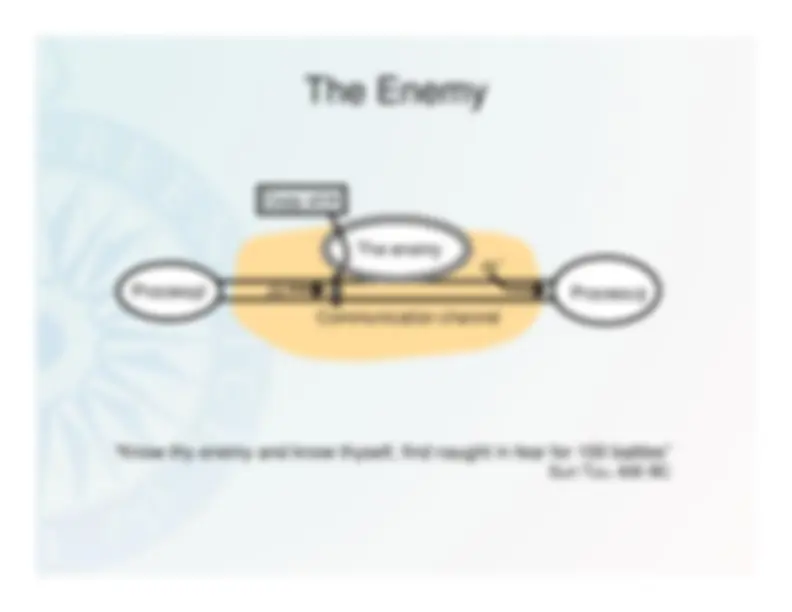
The Enemy^ Communication channel
Process
p^
Process
q
The enemy
m’
Copy of
m m
“Know thy enemy and know thyself, find naught in fear for 100 battles”
Sun Tzu, 600 BC
Methods of Attack
• Eavesdropping
– Release of message contents and trafficanalysis
• Masquerading• Message Tampering (Modification)
– Man-in-the-middle attack
• Replaying• Denial of Service• Mobile Code
Cryptography
- Caesar Cypher or Caesar Shift
- Substitutes a letter in a message by anotherletter– Substituted according to the length of a key– Example
Key = Caesar Message = THIS IS EASY TO CRACKMessage
= ZNOY OY KGYE ZU IXGIQkey
Terminology
Alice and Bob share a secret key K
.AB
1.^
Alice uses K
and an agreed encryption function E(KAB
, M)AB
to encrypt and send any number of messages {M
}KABi
to Bob.
2.^
Bob reads the encrypted messages using the correspondingdecryption function D(K
, M).AB
Alice and Bob can go on using K
as long as it is safe to assume that KAB
has notAB
been
compromised
.
Key challenges:
-^
Key distribution
and
Freshness of
Shared secret key communication
Authenticated communication
with a server
• Key challenges:
– Timing and replay issues
- These are addressed in Needham and Schroederand Kerberos
– Not suitable for e-commerce becauseauthentication service do not scale well
Bob has a public/private key pair <K
Bpub
, K
Bpriv
1.^
Alice obtains a certificate that was signed by a trustedauthority stating Bob's public key K
Bpub
2.^
Alice creates a new shared key K
AB^
, encrypts it using K
Bpub
using a public-key algorithm and sends the result to Bob
3.^
Bob uses the corresponding private key K
Bpriv
to decrypt it
Authenticated communication
with public keys
Summary of cryptography techniques • Symmetric (secret key)^ –
E(K, M) = {M}K – D(K, E(K, M)) = M – The same key is used for Encryption as Decryption– M must be hard (infeasible) to compute if K is not known– Usual form of attack is brute-force: try all possible key values for aknown pair M, {M}K. Resisted by making K sufficiently large ~ 128 bits
-^
Asymmetric (public key)^ –^
Separate encryption and decryption keys: Ke, Kd– D(Kd. E(Ke, M)) = M – depends on the use of a
trap-door function
to make the keys. E has high
computational cost.– Very large keys > 512 bits
Digital signatures with a secure
digest function
• Digest function – secure hash function
- takes a long string (or message) of any length asinput and produces a fixed length string as output
• THIS IS THE ORIGINAL TEXT = GRE3245AS144G
- notation H(M)– require that H(M)
≠^
H(M’) for all messages M..M’
• THIS IS THE ORIGINAL TEXTT = GD2T535RD7HG342• THIS WAS THE ORIGINAL TEXT = 45ER32657845TFG
Certificates
1.^ Certificate type
:^
Account number
2.^ Name
:^
Alice
3.^ Account
:^
4.^ Certifying authority
:^
Bob’s Bank
5.^ Signature
:^
{ Digest
( field 2 + field 3
)}^ K
Bpriv
•A statement signed by an appropriate authority (a CA)•Information is provided and certified by a CA•CA signs information using {Digest(F,F)}K
privB
•Others can check signature and validate the data using K
pubB
•But.. How is K
pubB
certified
•Requires another CA to provide K
pubB
•But.. How are they certified?
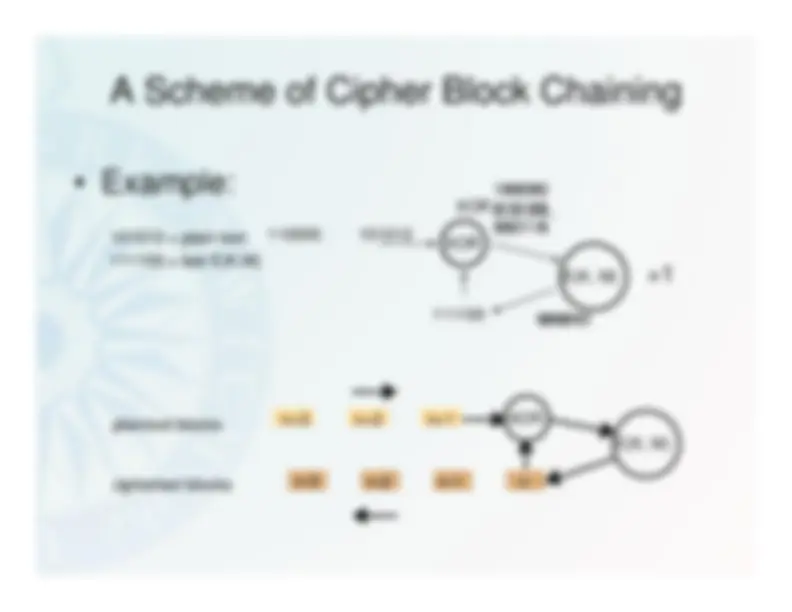
Cipher Block Chaining
- Eencryption algorithms use a set block size
(typically 64bits)
- Similar blocks result in similar encrypted
patterns
- This is a weakness that needs to be
overcome
- Solution – cipher block chaining with time
stamp initialization vector