





















Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
This document, 'comsm0213: what is security?' by e. Oswald and n.p. Smart, explores the concepts of security, confidentiality, integrity, and availability in the context of computer systems. The authors discuss various security threats, services, mechanisms, and policies to ensure secure data and systems. They also introduce security evaluation criteria such as tcsec, itsec, and common criteria.
Typology: Study notes
1 / 33

This page cannot be seen from the preview
Don't miss anything!


























E. Oswald and N.P. Smart
Department of Computer Science, University Of Bristol, Merchant Venturers Building, Woodland Road, Bristol, BS8 1UB United Kingdom.
April 8, 2010
E. Oswald and N.P. Smart
Definition of Security
When is something secure?
Security Analysis
E. Oswald and N.P. Smart
Confidentiality is about preventing unauthorised users reading information to which they are not entitled.
Traditionally, security and confidentiality are often identified.
Confidentiality is usually provided by encryption.
E. Oswald and N.P. Smart
Integrity is about making sure things are as they should be.
In the context of computing, integrity is about preventing unauthorised users writing information to which they are not entitled.
In a general system, integrity is about ensuring that the system state has not been modified by those not authorised to do so.
In the context of data communications, integrity is often restricted to detecting modifications or knowing where information comes from
Integrity is usually provided by MACs and digital signatures.
E. Oswald and N.P. Smart
Authentication is about knowing who an entity is, I (^) Before you allow them to do something.
We shall see how authentication is provided by various mechanisms such as I (^) Passwords I (^) Tokens I (^) Biometrics
We will also look at various models for ensuring authenticated entities only do what they are supposed to do.
E. Oswald and N.P. Smart
In practice not all improper actions can be prevented.
Thus users must be held accountable for their actions, including system misuse.
This is typically done by securely identifying users, and keeping an audit trail of security related events.
E. Oswald and N.P. Smart
In the “real world” a large amount of effort in security is about justifying a given product is secure.
Often the goal is to obtain a third party evaluation.
It is worth understanding a little about how this works as it has influenced a lot of products.
E. Oswald and N.P. Smart
Trusted Computer Systems Evaluation Critera (1983-1999) I (^) US system known as “The Orange Book” I (^) Used to evaluate mainly operating systems I (^) Six classes C1,C2,B1,B2,B3 and A1. I (^) Biased towards confidentiality and govenment applications
A system to get a rating had to meet certain specified functional requirements. I (^) Mandatory access control (see later) not required till B
Also needed to meet certain specified assurance requirements. I (^) e.g. testing, design specification and verification, documentation etc etc
E. Oswald and N.P. Smart
Criteria creep over time I (^) More stuff added at each level I (^) How to compare a C2 OS in year X with one in year X+2?
Testing took ages I (^) Testing done by evaluation labs seperate from the vendors and approved by govenments.
Two different regimes I (^) OK if only selling in one country, but by early 1990s we had a global economy.
E. Oswald and N.P. Smart
This is what is currently used (1998 onwards) I (^) Vendor defines a protection profile (PP) stating what the security requirements are I (^) Vendor defines a security target (ST) defining what is tested I (^) CC defines an evaluation methodology so one countries testing labs are equivalent to anothers. I (^) CC defines certain requirements for specific subsystems to obtain certain Evaluation Assurance Levels (EAL) I (^) The CC requirements are both functional requirements and assurance requirements Often the ST follows from the PP
E. Oswald and N.P. Smart
Another way of defining security, particularly in the case of systems other than computers, is to first perform a threat analysis.
Security can then be defined in terms of combating the perceived threats.
Not all threats are always worth defeating I (^) Need a Cost/Benefits Analysis
Risk Analysis This notion of assessing the importance of each threat, thereby leading to an assessment of whether it should be combated, is the essence of risk analysis. I (^) The cost of living with some threats (e.g. low level theft which can be quantified) may be less than the cost of prevention.
E. Oswald and N.P. Smart
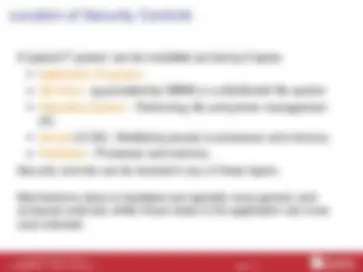
Next consider (in general terms) how security can be provided in a system.
What general types of security control exist, and where can these be located?
Security provided in an application can be subverted by attacking the operating system.
Security provided in the OS can be subverted by attacking the hardware.
Designing security into a system from the start is much better than adding security as an afterthought.
E. Oswald and N.P. Smart
A typical IT system can be modelled as having 5 layers I (^) Application Programs I (^) Services : eg provided by DBMS or a distributed file system I (^) Operating System : Performing file and printer management etc. I (^) Kernel (of OS) : Mediating access to processor and memory. I (^) Hardware : Processor and memory. Security controls can be located in any of these layers.
Mechanisms close to hardware are typically more generic and computer-oriented, whilst those close to the application are more user-oriented.
E. Oswald and N.P. Smart
An attacker with access to a system layer below where a security mechanism is located can bypass the mechanism.
Given system privilege access by the operating system allows one to bypass application program controls, I (^) e.g. by directly accessing files.
Given access to system hardware, the logical access controls of the operating system can be bypassed. I (^) e.g. to gain access to the hard drive on a computer unscrew it.
E. Oswald and N.P. Smart