


Study with the several resources on Docsity

Earn points by helping other students or get them with a premium plan


Prepare for your exams
Study with the several resources on Docsity

Earn points to download
Earn points by helping other students or get them with a premium plan
Community
Ask the community for help and clear up your study doubts
Discover the best universities in your country according to Docsity users
Free resources
Download our free guides on studying techniques, anxiety management strategies, and thesis advice from Docsity tutors
The second midterm exam for cs61b at the university of california, berkeley, taught by jonathan shewchuk in the fall of 2006. The exam covers topics such as binary search, 2-3-4 trees, and directed graphs.
Typology: Exams
1 / 3

This page cannot be seen from the preview
Don't miss anything!


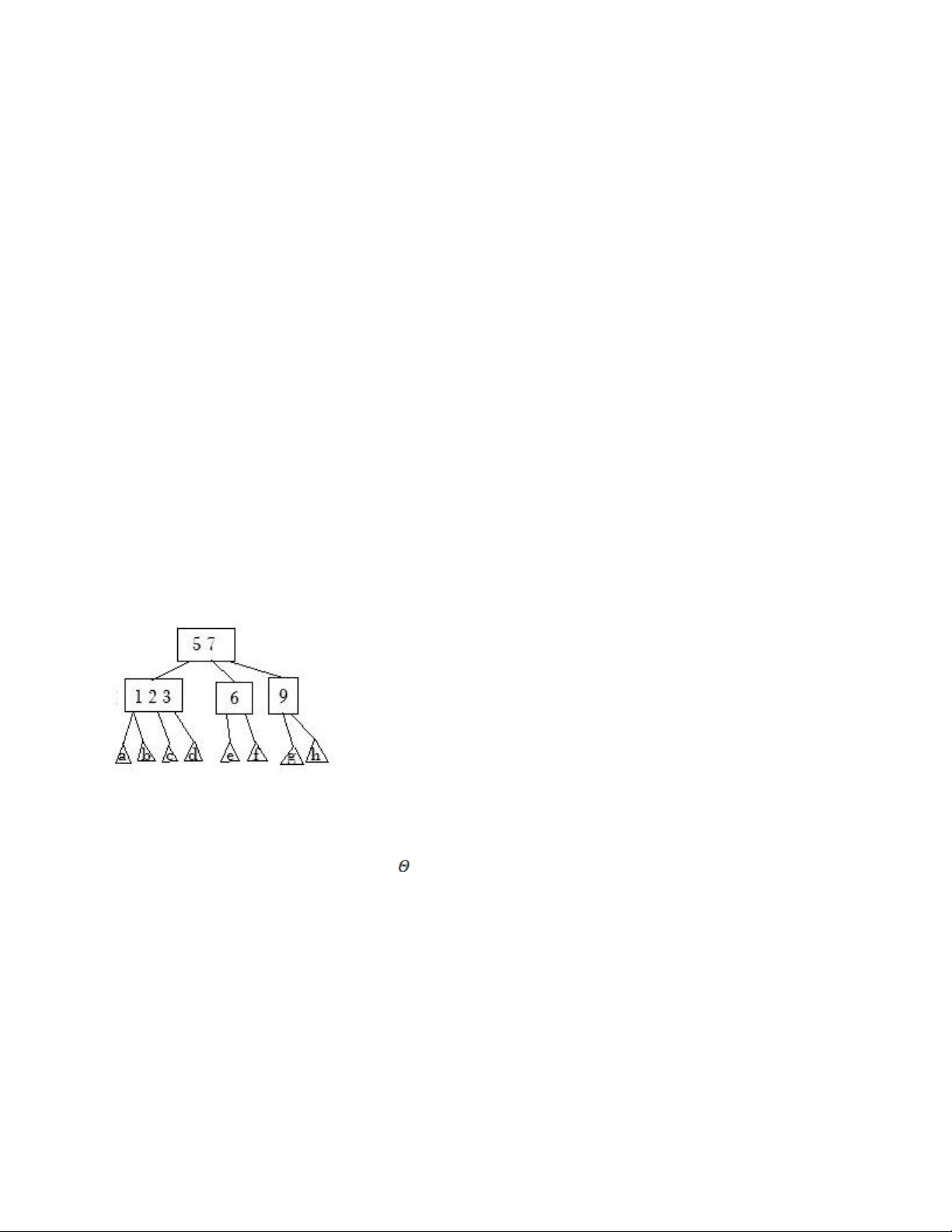
CS61B: Fall 2006, Midterm Exam II, Jonathan Shewchuk Problem 1. (7 points) A Miscellany a.(1 point) Suppose you implement a binary search method and it takes 10 microseconds to search a 1,000,000-int array for a number that turns out not to be in the array. How long do you estimate it would take for your implementation to search a 1,000,000,000,000-int array for a number that’s not in the array? b. (2 points) Explain why (1/(n-100))Є O(n). Don’t just reiterate the definition of big-Oh; give specific values of c and N that support the claim. (No need for a complete proof, though.) c. (2 points) When we remove an item from a 2- 3 - 4 tree, sometimes a node tries to “steal” a key from a sibling by performing a rotation. However, the remove algorithm we learned in class only allows a node to steal from an adjacent sibling. But there’s no fundamental reason why a node couldn’t steal a key from a nonadjacent sibling, except that we wanted to keep the algorithm as simple as possible. Show how we could modify the 2- 3 - 4 tree below so that the “9” node has one more key, the “1 2 3” node has one fewer key, every other node has the same number of keys it had before, and the tree is still a valid 2- 3 - 4 tree containing the same keys it had before. The triangles at the bottom are subtrees, which you cannot restructure (but you can change their parents). d. (2 points) Fill in the blank. The worst-case running time of the following method, expressed as a function of the input parameter n, is in (___________________________________________). Note that the loop does not use “i - - “! public static void weirdo(long n) { Tree234 tree = new Tree234(); //Construct an empty 2 - 3 - 4 tree. for (long i = n; i > 1; i = i / 2) { tree.insert(i); } } It’s not quite like the running time of any other algorithm you’ve seen. An explanation of your reasoning might help you get part marks if your answer is wrong.) Problem 2. (7 points) Binary Trees.
a. (2 points) Draw a tree that is both a binary search tree and a complete binary tree, and whose keys are the integers 1 through 9 (each appearing once). b. (2 points) If you perform the operation remove (5) on a binary search tree, it will obviously delete 5 from the preorder traversal of the tree. For example, if the preorder traversal was 5 2 1 3 4 before the deletion, then it is 2 1 3 4 after the deletion. But can the operation remove(5) ever change the order of keys in a preorder traversal? If “yes,” give an example. If “no,” explain why. c. (3 points) Show the sequence of swaps by which the method bottomUpHeap converts the following array into a heap. Redraw the array once for each swap (in the boxes provided). (Note: We’ve provided room for up to seven swaps, the maximum number possible for eight items. That doesn’t necessarily mean that this particular example takes seven swaps.) d. (0 points) If you could choose to be a tree, what kind of tree would you be? Problem 3. (9 points) Directed Graphs.